SaaS cloud security tools are also known as vulnerability assessment tools and they are as critical to your security posture, as your git repository or CI/CD pipelines are to your software delivery. They offer a lot of benefits for your organizations, developers, and consumers while helping them follow the modern cybersecurity guidelines easily.
However, the path to SaaS cloud security can be challenging.
With NIST mentioning a thorough guideline for application security and cloud infrastructure, it can be overwhelming for your development team to oversee all the changes all at once. And on top of that "Shadow IT" remains a challenging sphere for many medium to large organizations.
Opting for cloud security as a service from the best SaaS provider and shifting left is the way to move forward.
SaaS application security tools can help in threat detection in real time and protect your applications with each new update that is released.
But before we talk about tools, let me help you understand the nuances of SaaS security; its challenges and the software security best practices you can follow to protect cloud infrastructure and applications.
What is SaaS Cloud Security?
SaaS cloud security is a combination of the right security policy, enforced by prevention systems, which should include continuous monitoring, and conducted as part of a thorough SaaS security posture management framework that helps to patch potential threats, and secure cloud applications that are hosted with cloud service providers like AWS, GCP, Azure and others.
Now this is a very generalized security checklist for cloud security, but this area of cyber security is becoming increasingly important as enterprise applications and workloads move to public clouds and business processes become more dependent on cloud services.
SaaS security assessment tools provide the flexibility and accessibility of cloud computing that ensure you follow security measures to protect data and applications.
Importance of SaaS Security
Your SaaS applications need layers of security to minimize the effects of potential security incidents and allay the security concerns of your customers.
Increasingly, SaaS companies aiming building towards a more mature security model are relying on a combination of security professionals, allied with a shift left approach and the right DevSecOps software to not only increase their actual level of security, but also to reduce the burden on their security teams.
Their security strategies usually include the constant use of an API security tools to protect their SaaS apps against suspicious activities like unauthorized access, data breaches, malware and other OWASP Top 10 and SANS CWE 25 vulnerabilities.
These types of SaaS application security tools helps your development and security teams test security controls within your apps and APIs, particularly critical controls like authentication and access management, secure database operations and encryption and others. By doing this you're able to secure your users' sensitive data and become known as a security-conscious SaaS company.
Here's what happens with SaaS cloud security is done well.
Secure your cloud platform and help your SaaS customers keep their faith in you
Cynet reports that while most customers trust their service providers to handle security, according to research by McAfee only 18% of SaaS providers support multi-factor authentication and only 10% encrypt data at rest.
Some of your more security-conscious customers will ask you to implement single sign-on (SSO) for ease of deployment as well as to increase compliance with their own security solutions.
However, the overall burden for cloud security is on you. Also, contrary to some schools of thought, your chosen cloud provider puts that responsibility on you and therefore your software development process needs to properly equipped to find and fix security issues proactively, rather than reactively.
If your SaaS is hosted on AWs, here are 47 AWS security controls you can put in place for free.
Business requirements vs security requirements
SaaS applications, particularly those that are targeted towards FinTech and banking, need to comply with industry-specific regulatory compliance requirements.
However, Audacix clients who effectively manage their actual security posture go beyond the requirements of their security certifications to proactively manage both insider threats and external threats.
Essentially their approach to security transforms from something that is just done as part of a security checklist to one where their business relationship with users is based on minimizing cloud security failures, thereby building trust with their customers quicker.
This is why Cyber Chief's 3-in-1 approach to effective security for cloud applications becomes such a no-brainer?
Why? Because it helps you take care of web app security, API security and cloud security posture management.
Minimizing business disruption
Last but most important, automated application security tools help you to avoid major business disruptions that can be caused by a security breach. Disruptions caused by to exploitation of security issues can sometimes lead to months or weeks of disruption in your business.
But it's not just a cyber attack that causes disruption. Before software teams started working with us, they would lament the fact that vulnerability patching took too long and developers became disenfranchised.
Unfortunately, this type of business disruption is all-too-common, but it doesn't need to be that way.
One of the ways in which you can protect your applications and cloud environment is by adding an automated vulnerability assessment tool such as Cyber Chief.
While many tools, or even SaaS security service providers, will be able to provide you with analysis reports, Cyber Chief will give you those reports in a couple of clicks, without having to send an email or wait for a vendor to respond to you.
Your developers can use these remediations, which often include code snippets, to fix exploitable vulnerabilities.This eliminates the need to consult security experts for every new update for your applications - thereby saving you time and money while bumping up your SaaS security posture management.

Key Components of SaaS Cloud Security
Combatting security threats in modern enterprises requires a number of defense vectors. There's no doubt you need the right security practices, including thorough software security reviews. But your decisions also need to ensure that you're reducing, not adding to the challenges for security teams.
In order to reduce this pressure here is the minimum viable security infrastructure you need for your cloud-based applications:
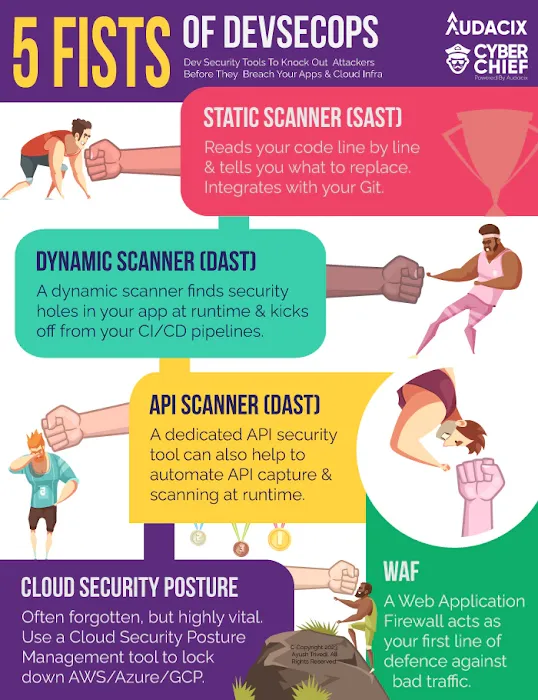
5 Fists of DevSecOps: the most efficient SaaS cloud security stack
- Static Application Security Testing (SAST):SAST tools analyze your code for coding practices that could lead to vulnerabilities. This helps developers write secure code from the start, saving time and effort.
- Dynamic Application Security Testing (DAST): DAST tools assess your applications in their runtime environment, offering a more comprehensive view of potential vulnerabilities.
- API Security: the best API security tools go beyond traditional security measures to uncover hidden security risks in your APIs, providing you with instant alerts and insights into potential vulnerabilities.
- Web Application Firewall (WAF): WAFs prevent unauthorized access and safeguard against common attacks like SQL injection and XSS, helping you maintain customer trust and safeguard sensitive data.
- Cloud Security Posture Management (CSPM):CSPM tools help you identify vulnerabilities in your cloud environment by analyzing the security configurations of your cloud console and services.
The reason we call this the "minimum viable security infrastructure" for SaaS apps and APIs is because each of these tools can be further divided into smaller parts.
We've also excluded user access/authentication methods because they form a part of our application architecture-related decisions.
And just to be clear, end-to-end SSL encryption and settings like transport layer security (TLS) are now hygiene factors rather than nice-to-haves.
You can read more about our 5 Fists of DevSecOps or download our application security checklist if you want to see where you currently stand.
Do outsourced development teams also need such a comprehensive approach?
In short: yes.
In fact, our top clients who outsource much of their critical application development automate cloud security activities than many companies who have internal development teams.
The reason for this is simple - a high standard of SaaS security posture management becomes increasingly difficult as your amount of outsourced software development increases.
Automating gives you power close to complete control over the unified security posture for both third-party applications as well as core business apps.
What about giving your SaaS developers' security training?
Security training for developers exists because most developers are completely unaware of the security implications of the code they right.
Unfortunately, traditional, classroom-style or virtual security training has its limitations. Developers will only remember a small percentage of what they're taught in such sessions and will implement even less in their day-to-day work.
This is where Cyber Chief can help you with On-Demand Security Coaching capability.
On-Demand Security Coaching allows your developers to have their questions answered as they are actually patching security vulnerabilities. For Cyber Chief users, this means that vulnerabilities are patched on average within hours, rather than days or weeks.
Imagine what you could do with all that extra productivity?

What Can You Do For Your SaaS Cloud Security?
Have a look at our thorough pentesting-as-a-service offering for "done-for-you" solution that will take care of your cloud and application security headaches.
Or, if you prefer to do it yourself, you can protect your SaaS applications with automated security testing tools such as Cyber Chief because it can help you handle 3 key aspects with in one place:
- End-to-end API security for REST, SOAP and GraphQL APIs.
- Web application security testing.
- Cloud security posture management.
Most importantly, while other tools just highlight vulnerabilities and leave your development team on their own for patching, Cyber Chief will help your devs ensure that your AppSec risks are patched (almost) as quickly as they are found.
To see how application security automation can help modernize your application security program give Cyber Chief a try or book your discovery call to see if it might be a good fit for you.