- What are penetration testing services?
- What is the difference between vulnerability assessment and penetration
- How can I perform a web app vulnerability assessment?
- Why do I need a penetration test?
- How much does a penetration test cost?
- How can SaaS companies perform a penetration test on a budget?
- How long does a penetration test take?
- How to choose a top penetration testing company?
- What do top penetration testing companies do that their competitors don't?
Choosing the best penetration testing company can seem like a daunting task. If you're the process of selecting your web application penetration testing vendor and if you don't know how or why to make a final decision - your're not alone.
It's easy to become confused and lost in all the jargon. "Enumeration" this. "Hardening" that. "Security posture" this. "Security controls" that.
I've broken it down for you using as much common-sense as I could muster (it might actually blow your mind!).
The unfortunate fact is that most penetration testing service providers do a really horrible job of helping you, the customer, understanding four critical decision-making questions:
What type of penentration test do you need?
-
How will their penetration testing services actually help you (beyond a 50-page penetration test report)?
-
How to build a culture of security within your SaaS development team?
- How can you automate testing security of a website and run AppSec from your SDLC?
It is the answer to that last question where much of the value actually sits for you!
Most penetration testing services are sold with the intention of having you, the customer, come back to the pen testing company year after year. In order to get your repeat business, they forget to explain just how you can build a repeatable, scaleable and consistent application security structure within your software development teams.
Which probably explains why not enough pen tests are actually conducted on cloud software around the world!

But let's start with some of the key questions around choosing a top penetration testing company for your unique use case and types of applications.
What are penetration testing services?
Penetration testing services are in-depth security tests of your cloud and on-premise networks, web applications, mobile applications, APIs and SDKs.
When you choose to partner with a top penetration testing vendor your penetration tests are performed by highly trained and accredited professional hackers and experts.
The point of these security tests is to simulate an attack by criminals or otherwise unauthorised users. The penetration testing service provider then tries to breach into your network and/or application, to identify the flaws.
No developer wants to create software with security holes. But, unfortunately, experience and statistics show us that old habits die hard and that only consistent and thorough SaaS security testing can actually keep your software, your users and your reputation secure:

Keep in mind that the top penetration testing companies also provide best practice security recommendations to help you patch your vulnerabilities.
Penetration testing services are a great way to test your system and identify the most likely places where your company will leak your own and your customers' sensitive data.
What is the difference between vulnerability assessment and penetration
Vulnerability assessments and penetration testing are two related but different activities. They are often concatenated into one term: VAPT.
Unfortunately, they are often also sold as one and the same service by unscrupulous penetration testing companies.
Basically, running even the best vulnerability assessment tool is like conducting an X-ray, whereas penetration testing, on the other hand, is like performing surgery. It goes beyond the surface and digs into the inner workings of the network.
Manual penetration testing is the process of testing a network, API or web/mobile application to find vulnerabilities that an attacker could exploit.
The goal of manual penetration testing is to identify security weaknesses and potential threats to the application so they can be fixed.
Because of the shift to the cloud, network penetration tests for cloud platforms like AWS are also necessary - especially as your team grows and more people have access to your cloud platform.
A vulnerability assessment scans a website or web app's surface, identifying weaknesses in its security without going deep into a network and breaking anything. The best automated penetration testing tools can also scan your application behind your login. This is often called authenticated vulnerability scanning.

Security for web applications, APIs pentesting, mobile application penetration testing and cloud penetration testing is done by security professionals on your network and applications. These experts deploy different hacking methods to break into your system and find holes that an automated vulnerability assessment might not have found.
While a vulnerability assessment may tell you where the security vulnerabilities are, a penetration test will give you proof of that the vulnerability is in fact real and that you need to patch it to avoid future security exploits.
How can I perform a web app vulnerability assessment?
A web application vulnerability assessment can be performed by using many different vulnerability scanners that look for critical vulnerabilities in your web apps and APIs.
List like the OWASP Top 10 and SANS CWE 25 are useful if you're trying to understand the critical vulnerabilities that you should look for and eliminate from your application.
Contrary to popular belief, you don't need a penetration testing firm to help you conduct a vulnerability assessment . You can and should do it yourself using the web app security assessment tools that are user-friendly and built to be used by software dev teams. Ideally, every time you are about to ship a new release of your application, or at the very least, daily.
There are a select few of the best vulnerability scanning tools that are actually built for software development teams. Our tool, Cyber Chief, integrates with your software deployment pipelines and allows you to run authenticated and unauthenticated vulnerability scanning on each of your application environments.
Even if you don't have the budget for full-blown manual penetration testing, you should invest in a vulnerability scanning tool like Cyber Chief to help your developers shift left with security.
Why do I need a penetration test?
Penetration testing is a method that evaluates the security control of your premises to determine the best possible improvements to your web application's security posture.
Penetration testing is based on real-time security tests that use advanced hacking techniques to determine weaknesses in a security posture.
Advanced penetration tests can simulate attacks on your networks in the same fashion to detect active attacks on the network.
Unlike automated penetration testing tools or vulnerability scanning tools, an ethical hacker performs penetration testing and is therefore able to apply her intellect and creativity to mimic real world attacks.
No automated tool is yet advanced enough to be able to completely eliminate the need or deliver the insightfulness of manual penetration tests.
How much does a penetration test cost?
Manual penetration testing is performed by highly skilled cyber security experts who are trained to simulate real world attacks on critical systems. Because of this significant human element the costs vary significantly based upon the size of the organization and the number of web apps, mobile apps and/or APIs that are to be tested.
Typical (there's no such thing as a typical pen test!) web application
penetration tests can cost anywhere between $7,000 to $75,000, depending on
the team size, the penetration testing scope and any other cyber security
solutions that may be included in the package.
That's a big range, I get it. But like the length of a piece of string, there is no one, easy number that I can give you for your security testing project, without getting more details from you.
Modern application security demands have spawned the rise of more robust approaches. One such model is the pentesting-as-a-service solution, which includes on-demand, self service application security tools, backed by targeted services from expert penetration testers when your team needs it.
The good news for you is that there are ways to cut your cost of pen testing for web apps and mobile apps.

Large enterprises usually pay a daily rate to their penetration testing providers because they have large network security requirements and complex cyber threat situations that require advanced penetration tests by experienced penetration testers.
This is in addition to any enterprise-grade application security tools they may have invested in for application security automation.
Naturally, when you add real-time detection and response capabilities, you can understand why the cyber security solutions budgets of medium to large enterprises are skyrocketing!
How can SaaS companies perform a penetration test on a budget?
Most CTOs and software development managers in SaaS companies have to balance spending on testing security of websites with their growth objectives (investors need to be kept happy, right!).
Application security investments are like insurance policies. The annual payments might rankle you, but you end up smiling ear to ear when that same policy helps you dodge one of life's unexpected fires.
If you fit this boat, then you'll be intrigued to know that there are ways to cut the cost of your web application penetration testing (and for mobile apps too).
How long does a penetration test take?
The length of a penetration test again depends on the penetration testing provider, the penetration testing scope and size of the network or application undergoing the security assessment.
Your web application penetration test can take anywhere from 1 to 4 weeks to complete, depending on the size and complexity of the application.
It is important to remember that each penetration test is unique, and may require more or less time than specified above.
You can use these timelines as a rough rule of thumb:
-
A black box web app penetration test or network pen test for a small to medium sized network will take approximately 1-2 weeks until your penetration test report is delivered.
-
A gray box web app pen testing process, where your software security is assessed without logging in and after logging in, can take 2-4 weeks depending on the size of your application, number of user roles and APIs that need to be tested.
-
A white box web application pen test is the most in-depth type of web or mobile app security testing you can perform. On top of everything that is done for black and gray box pen testing, white box penetration testing involves reading and scanning your code base, line-by-line. It's easy to understand, then, that white box web app penetration testing can take 4 weeks or longer.
A critical component of our security testing team's communication process is to let you, our client, know at the start of the project how long your security evaluation will take. And then update you again 1 week into the project to confirm timelines.

Want to see how a pen testing company that understands software development can take a load off your shoulders & coach your developers at the same time?
This helps you plan your software development team's workload to leave enough capacity for them to be free to fix critical vulnerabilities when you receive the penetration testing report.
A focus on clear and consistent communication is why the smartest SaaS teams like Clevertap, Rudderstack, Opal.dev and others give us 5 stars and consider us amoung the best penetration testing companies that they have partnered with.
The added bonus is that working with Audacix gives you access to application security automation with a powerful and user-friendly web application security tool and on-demand coaching to ensure that your devs are never left to fend for themselves.
How to choose a top penetration testing company?
When partnering with a penetration testing company, it is best to stay away from ethcial hacking companies that don't understand the software development workflow.
There are a lot of penetration testing companies that will tell you they are “the best” in the field, but most of these companies find it really difficult to articulate what that means for you and how you will be benefit from their greatness.
Having spoken to our penetration testing clients about the factors that they considered when trying to maximise their ROI from penetration testing services, we were able to distil their answers down to 7 key questions.
As a client you will not know how to answer all of these questions, unless you have had the experience of working with one of the top penetration testing companies in the past.
But simply asking these questions of prospective penetration testing companies will help you guage just how they will work with you in the future and whether there is a cultural fit between both your teams.
Keep in mind that you will still need to work with your chosen partner to understand the best penetration testing services that will give you the results that you want.
Before you roll your eyes at my suggestion of achieving a cultural fit with your pen testing partner. Consider this as just one of the reasons why achieving this fit is so, so imnportant in this day and age:

So, how do you choose the best penetration testing company for you? Ask the right questions:
Q1: How will your penetration testing services help me acheive the highest ROI for my investment?
The biggest problem with cloud cyber security testing services is that the people who sell and perform them often forget that security testing services are an enabler of a greater objective.
You don't build your application to make it the "most secure application in its class," do you? Your application is built and enhanced to help your company achieve its commercial goals, right?
So what you need to understand by asking this question is how your security testing partner believes their services will help your company achieve your commercial goals.
I believe simply bridging this gap will help you achieve a massive outcome:

If they can't answer this in a succinct and meaningful manner, you're better off looking for a security testing partner that understands how they will help you improve not only your application security, but also your bottom line.
Q2: What frameworks will you use to perform your penetration testing services?
Most people I speak to in your shoes who have actually been through a web application penetration testing project cannot tell me what framework was used to conduct their last pen test.
You many not understand all the acronyms that are thrown at you, but you need to work out whether the framework that is being used to perform penetration testing is actually fit-for-purpose.
If you are a B2B SaaS company selling to larger enterprises or in the sensitive industries like FinTech or real estate SaaS or HealthTech, then its likely a waste of your money if your pen test is only performed to the OWASP Top 10 standard.
Let me put this to you another way. If you are in any of the industries/spaces above, a standard OWASP Top 10 pen test will not give you much more value than a report from an automated vulnerability assessment tool.
If this aspect is not made clear to you during the sales process, then you have to wonder at the transparency of the the penetration testing team, no?
Q3: How will you help our dev team minimise the time they spend fixing security vulnerabilities?
Believe it or not, many penetration testing services companies don't believe it necessary to provide detailed (or any) recommendations/fixes for the vulnerabilities they identify.
Essentially, they are leaving you to swim alone with the sharks (without a cage). That is seldom a fruitful or enjoyable exercise.
You must expect more and you must ask the questions at the outset to understand how your pen testing partner will get you what you need.

Do you want to see a turnkey application security structure that includes on-demand self service tools + frictionless penetration testing services?
Q4: Will you conduct an automated security scan or full gray-box manual penetration test?
It's no fun paying for a mango, but receiving a lemon in return. So clarify up front whether the service you are receving is a glorified automated vulnerability scan that takes a few hours, or an actual manual penetration test performed by skilled and creative ethical hackers.
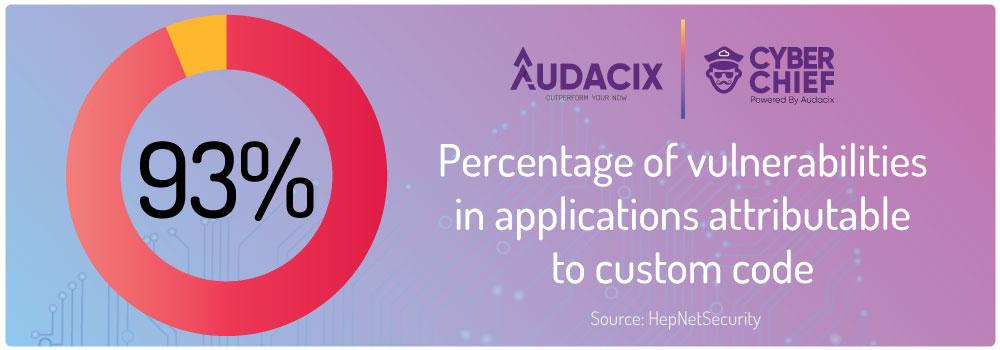
Q5: How can you support us if we want to get or maintain our ISO27001 or SOC2 certifications?
As a B2B SaaS company ISO27001/27015 and SOC2 are must-have certifications if you want to prove your "enterprise-readiness".
If you have these certifications or will complete these certifications in the future, then you must choose a penetration testing company that can:
-
Provide guidance on the types of penetration testing services that will help you get and stay certified; and
-
Help you create, prepare and/or upgrade your information security management systems to stay compliant with your chosen certifications.
The last outcome you want is to pay good money for ISO27001 or SOC2 security testing services and then find out that your auditor doesn't believe the pen testing was done to a robust-enough standard or that your security controls are not up to the mark!
Q6: Can your team help us in patching our application security vulnerabilities?
It might suprise you to learn that most ethical hackers are not software developers. In fact, most of them couldn't write a coherent line of code to save themselves!
Coding is a skill that is not required for them to play their roles. Obviously the best penetration testers have coding ability and this allows them to employ a level of creativity that is a cut above - and this shows in the vulnerability resolutions that they provide in their reports.
So in case your software development team doesn't have the ability or capacity to patch vulnerabilities identified during your application security assessment, don't just assume that your pen testing partner will help you patch those vulnerabilities!
Q7: How will you help us ensure that the security vulnerabilities don't re-appear during future sprints?
This question will stump many a good pen tester. Some might even tell you that it's not their job to give you this result (run the other way if you hear this reponse!).

Do you want to try a vulnerability scanner that is user-friendly, built for software devs & helps you ship your software with zero known vulnerabilities?
The best penetration testing companies will show you they will help your devs find and fix vulnerabilities in between your manual pen tests.
By listnening to their answer to this question, you should clearly understand how they will help you shift left with application security and reduce your reliance on them - no matter how amazing they are.
What do top penetration testing companies do that their competitors don't?
The cyber security experts at top penetration testing companies are aware of the latest trends and vulnerabilities, because this trait helps them to hold some of the edge against their competition.
However, technical proficiency will only go so far. As a consumer of penetration testing services you should consider technical proficiency a hygiene factor. Your preferred security testing partner is either technically excellent, or they aren't, in which case you move on.
There are 5 principles that I believe separate the wheat from the chaff when it comes to the best penetration testing companies and what they can offer you during every security testing project:
Going beyond security: do they understand that security is one part of the puzzle you're trying to solve and can they help you solve more pieces of this puzzle, beyond security?
Transparency: do you have to go poking and prodding to get information from them or do they transparently bring it to your attention?
Education: few developers love classroom-style security training. So is the pen testing company able to educate your developers on-the-job while providing their services?
Integrity: do you feel like you can trust them? It's a short question, but not a simple one to answer.
Scalability: can they help you reliably scale your security activities by helping you shift left with application security, without adding huge amounts to your developers' existing workload?
Now that you have all the knowlege you need to choose a top pen testing partner, do you want to see what it all looks like in practice?





